Dramatically improve your Joomla site security using SSH keys
Secure shell protocol (SSH) exists to keep your connections secure. SSH can be difficult to grasp as it involves a complex set of security tools which can be a challenge to understand. But don't give up. You are dramatically less likely to be hacked if you use SSH connections with keys properly.
Passwords are bad, keys are good
Passwordless secure connectivity between trusted computer accounts and your Joomla CMS is well worth getting going. If there's no password, theres no opportunity for that password to be brute forced, weak, or blank, and you know that the only computer account that can connect that way is the one with the right key so your security is massively improved from attackers immediately! This article shows you how to do it and explains the parts of the technologies needed and no more.
What you'll find out
- Just enough about SSH to make your command line access secure
- Joomla CMS access via the terminal and why it needs SSH
- Implement SSH keys for your Joomla site to enable command line access without passwords
- Use the Joomla API from the command line to get stuff done
- Recap of the benefits of key based SSH authentication
TL:DR – The benefits outweigh the costs by far. Nobody will visit a web site that isn't secured by SSH anymore. And SSL certificates are free! All it takes is a little bit of thought and you literally never have to think about it again.
Contents
- Dramatically improve your Joomla site security using SSH keys
- Passwords are bad, keys are good
- What you'll find out
- Using keys with Secure Shell Protocol (SSH) to dramatically improve your Joomla Content Management System (CMS) Security
- Just enough about SSH to make your command line access secure
- Joomla CMS access via the terminal and why it needs SSH
- What can happen if I dont secure my Joomla site?
- Hands-on lab — Implement SSH keys for your Joomla site to enable command line access without passwords
- Hosting provider portal settings for the site
- Generating your private and public SSH key pair
- Adding the key to the hosting providers control panel for your site
- Testing that it works by using the Joomla Command Line Interface (CLI) to get stuff done
- Recap of the benefits of key based SSH authentication
Using keys with Secure Shell Protocol (SSH) to dramatically improve your Joomla Content Management System (CMS) Security
- Learning Objectives
- Understanding just enough about SSH
- Joomla CMS access via the terminal and why it needs SSH
- Implement SSH keys for your Joomla site to enable command line access without passwords
- Use the Joomla API from the command line to get stuff done
- Recap of the benefits of key based SSH authentication
Just enough about SSH to make your command line access secure
At its core, SSH is a cryptographic network protocol that provides a secure channel for data exchange, effectively shielding sensitive information from potential threats. such as interception, eavesdropping, or unauthorized access. SSH provides protection from these threats.
SSH operates by establishing a secure and encrypted communication tunnel between two devices. The encryption ensures that the data traveling through this tunnel remains confidential, shielding it from prying eyes. SSH can employ cryptographic keys—a pair of public and private keys—as authentication credentials to completly avoid passwords for connections.
When a connection is initiated, the client and server exchange a challenges which uses these keys. The public key is freely shared, while the private key remains secure. This two-key mechanism ensures that only authorized parties (those with the private key) can establish a connection. It's like having a lock and key for a specific door—only the designated key can unlock the door.

By utilizing SSH, you dramaticaly improve your digital connections against unauthorized access and data breaches. So much so that you should always be using SSH for any connection you have where you transfer or access data. SSH completely removes the risks associated with transmitting sensitive information over unsecured channels. Whether accessing a remote server, transferring files, or managing a website's content, SSH provides a secure way to go about these activities.
In a content management systems like Joomla, SSH's becomes even more important. Secure connections mitigate the chances of unauthorized access to crucial data. This can be particularly impactful when managing confidential user information, financial data, or sensitive business content.
In essence, SSH is the technical guardian for the security of digital connections, ensuring that information flows inside a secure conduit. Its role in Joomla CMS security is pivotal—a shield against potential that makes it possible for users to navigate their CMS structure with confidence.
Joomla CMS access via the terminal and why it needs SSH
Terminal access is dangerous. You can potentially read data anyplace within your Joomla site. You shouldn't allow terminal access to be easy to get to make your administration more convenient because if you do, you are making it easier to exploit. Key based SSH stops this from happening.
Joomla, like any web based platform is vulnerable to potential cyber threats. you already know that you should keep your site up to date, deploy the correct '.htaccess' site security override file, and that you should access the administration of your site only using the Joomla administration backend, with an administrator account not called 'admin' or 'administrator' and requiring a physical security key such as a 'Yubikey' or an authenticator program such as 'Authy'. If you haven't set those protections up you are asking to have your site compromised and you probably shouldnt be accessing your site from the command line at all.
What can happen if I dont secure my Joomla site?
But quickly, to recap, heres what can happen if you don't secure your site:-
- If you don't deploy an anti spam contact form technology like 'captcha' your site might be sending spam emails
- If you don't keep your site updated you can allow a known vulnerability to be exploited which might enable your site data to be accessed and stolen.
- If you don't deploy the '.htaccess' site security override file correctly you might allow a folder to be writeable that should not be, again allowing your site data to be accessed and stolen
- If you use just a password for the site administrator account you are inviting brute force password stealing scripts to try to break in to your site. Once they have admin access they can do whatever they like. Turn it into a porn site, send malicious emails, grab all your data and customer information
- The least bad action is defacement of your site where amateurs might put up a fake page to show off to their geeky friends. Malware and hidden scripts can also be deployed to mess up your site in the future and provide a real headache for cleanup.
These real-world examples of how improper security measures can lead to unauthorized access and data breaches should make you want to review your site security.
Hands-on lab — Implement SSH keys for your Joomla site to enable command line access without passwords
So lets implement key based ssh access to your site. there are several steps to this:-
- Hosting provider portal settings for the site
- Generating your private and public SSH key pair
- adding the key to the hosting providers control panel for your site
- Testing that it works by using the Joomla Command Line Interface (CLI) to get stuff done
Hosting provider portal settings for the site
- First of all you need to enable SSH access for your hosting provider. Not all hosting providers allow this so you may need to change if you need it. Every hosting provider is different, my site provider, Rochen, is the same provider that Joomla.Com is hosted by, and they are Joomla experts I would highly recommend. You enable SSH from their site management portal. It is enabled when the link says 'Disable'. You can see that below. Click enable and it will be enabled. Now you can ssh into your server, using your administrator username and password. If you have a different provider you'll need to find the setting to enable SSH. We are only part of the way there towards getting key based authentication going.
You can click disable to disable it. You might choose to enable and disable it here whenever you need it but if you have keys set up properly this is not necesssary.

Generating your private and public SSH key pair
This is easy to do on a Mac or a Linux computer or in the Windows Subsystem for Linux where all the tools are available from the command line.
- First check if you have an ssh key already. If you do have one, be sure to choose a unique name for this one so you can identify it afterwards and be aware that if you do not, your existing key will be overwritten.
- Open a new Terminal window. Type ssh-keygen -b 4096 -t rsa
- You will be prompted to enter a filename which will default to
id_rsa.pubfor the public keyid_rsaand for the private one. Change it to something memorable likeid_rsa_yoursitename.pubfor the public key andid_rsa_yoursitenamefor the private one. - When prompted, don't enter a passphrase.
- This process will create a hidden folder called .ssh in your home folder if it did not exist before that contains both your new public key (id_rsa_sitename.pub) and new private key(id_rsa_sitename.)
% ssh-keygen -b 4096 -t rsa
Generating public/private rsa key pair.
Enter file in which to save the key (/Users/username/.ssh/id_rsa): id_rsa_yoursitename
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in id_rsa_yoursitename
Your public key has been saved in id_rsa_yoursitename.pub
The key fingerprint is:
SHA256:9d921d76-396e-4bb5-9155-09ab69aac9c5 username@machinename
The key's randomart image is:
+---[RSA 4096]----+
| x E .*B+|
| . x +=.|
| xx 0oX|
| . x. = xBB|
| 0 x + = +|
| . + o . +.|
| + x =.o|
| x x .x*x|
| x x ..xx|
+----[SHA256]-----+
Adding the key to the hosting providers control panel for your site
This is probably the most complicated part to master. SSH keys are a confusing topic from the start, but the language used can also be difficult to interpret. Lets go for it and remember all we want is for one key to be able to be used to connect a terminal between our Mac or Linux computers local user account securely, to the command line interface (CLI) in your Joomla CMS Site.
- Find 'SSH Access'

Your site administration tools should have an SSH Access component, this is from 'cPanel' yours might be different - Under SSH Access you'll see the following text or similar:-
SSH allows secure file transfer and remote logins over the internet. Your connection via SSH is encrypted allowing the secure connection. In this section you can manage your SSH keys to allow automation when logging in via SSH. Using public key authentication is an alternative to password authentication. Since the private key must be held to authenticate, it is virtually impossible to brute force. You can import existing keys, generate new keys, as well as manage/delete keys.
SSH (Secure Shell) is a program to log into another computer/server over a network securely. It provides strong authentication and secure communications over insecure channels. Your login, commands, text are all encrypted when using ssh.
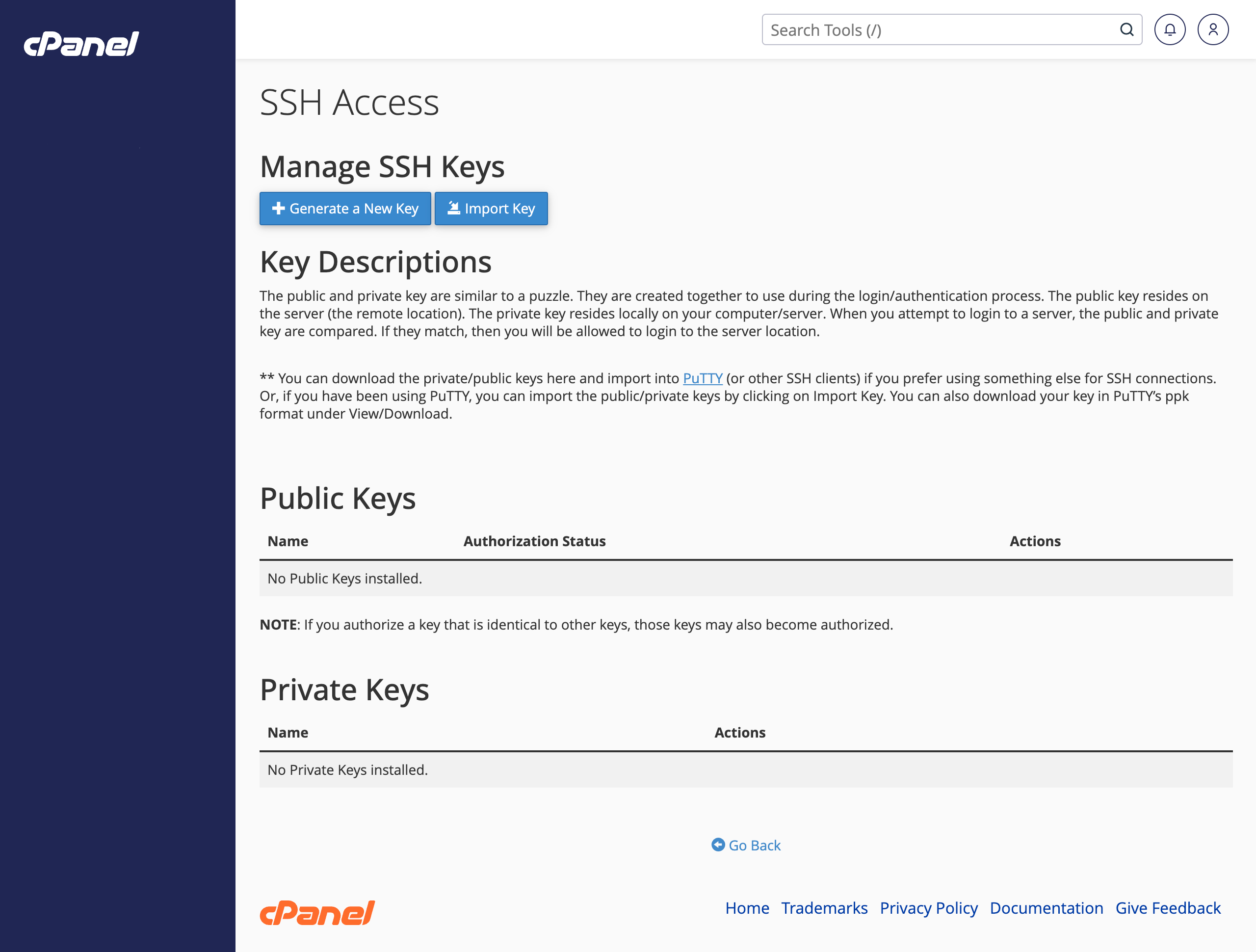
The public and private key are similar to a puzzle. They are created together to use during the login/authentication process. The public key resides on the server (the remote location). The private key resides locally on your computer/server. When you attempt to login to a server, the public and private key are compared. If they “match”, then you will be allowed to login to the server location. - Look for the button labeled 'Manage SSH Keys' and click it
- On the bext page click 'Import Key', bwcause we are using the key we just created on the local computer.
Managing SSH keys in cPanel - In the
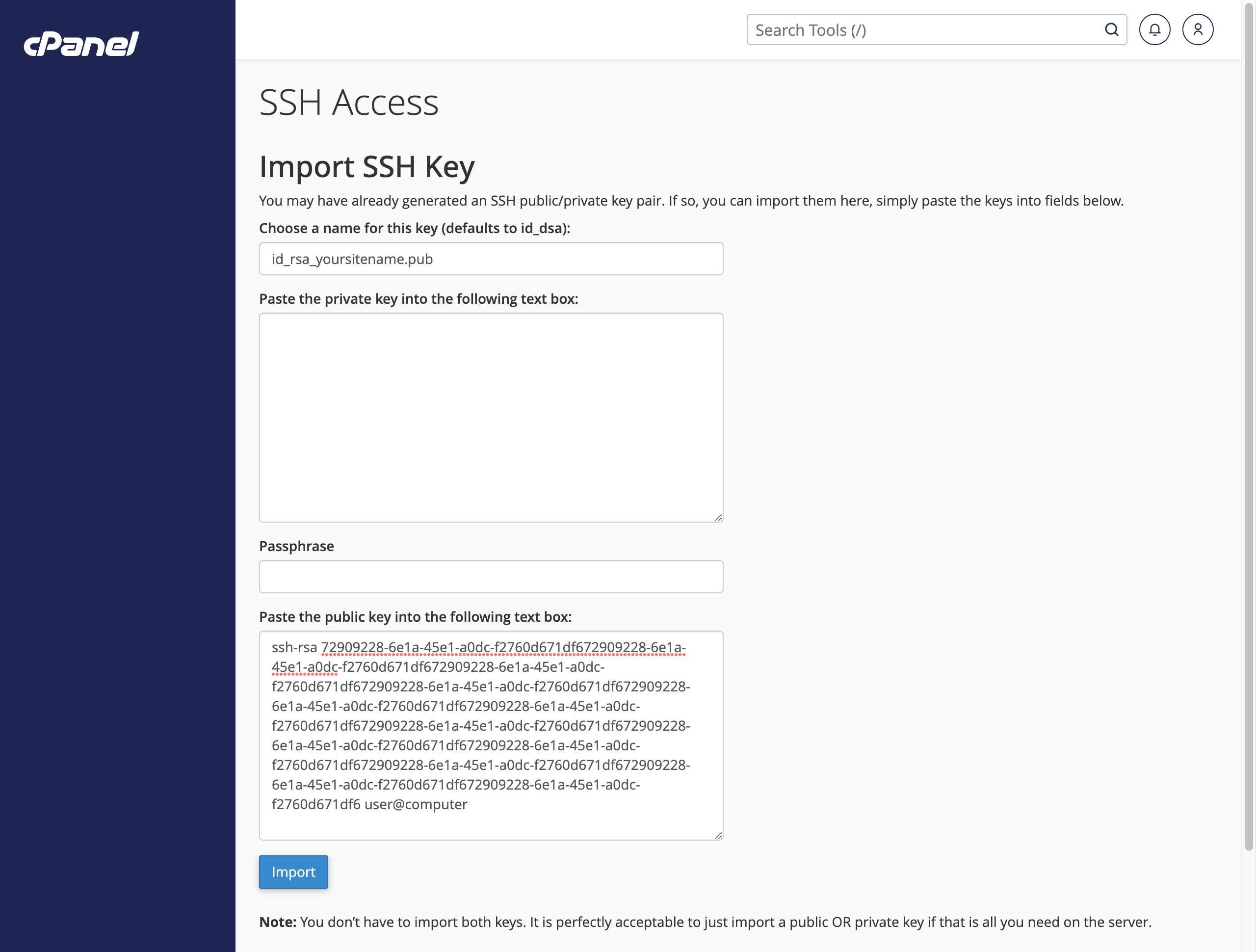
Choose a name for this key (defaults to id_dsa):form field typeid_rsa_yoursitename.pub - Copy the contents of the public key file into the
Paste the public key into the following text box:form field. On a mac you can usepbcopylike this cat ~/.ssh/id_rsa_yoursitename.pub | pbcopy and then paste it into the field using ⌘ V It should look something like this and note its just the public key we want on our Site, not the private key. This form can do both, and its confusing!
Importing the SSH public key to cPanel - You should get a success message like this

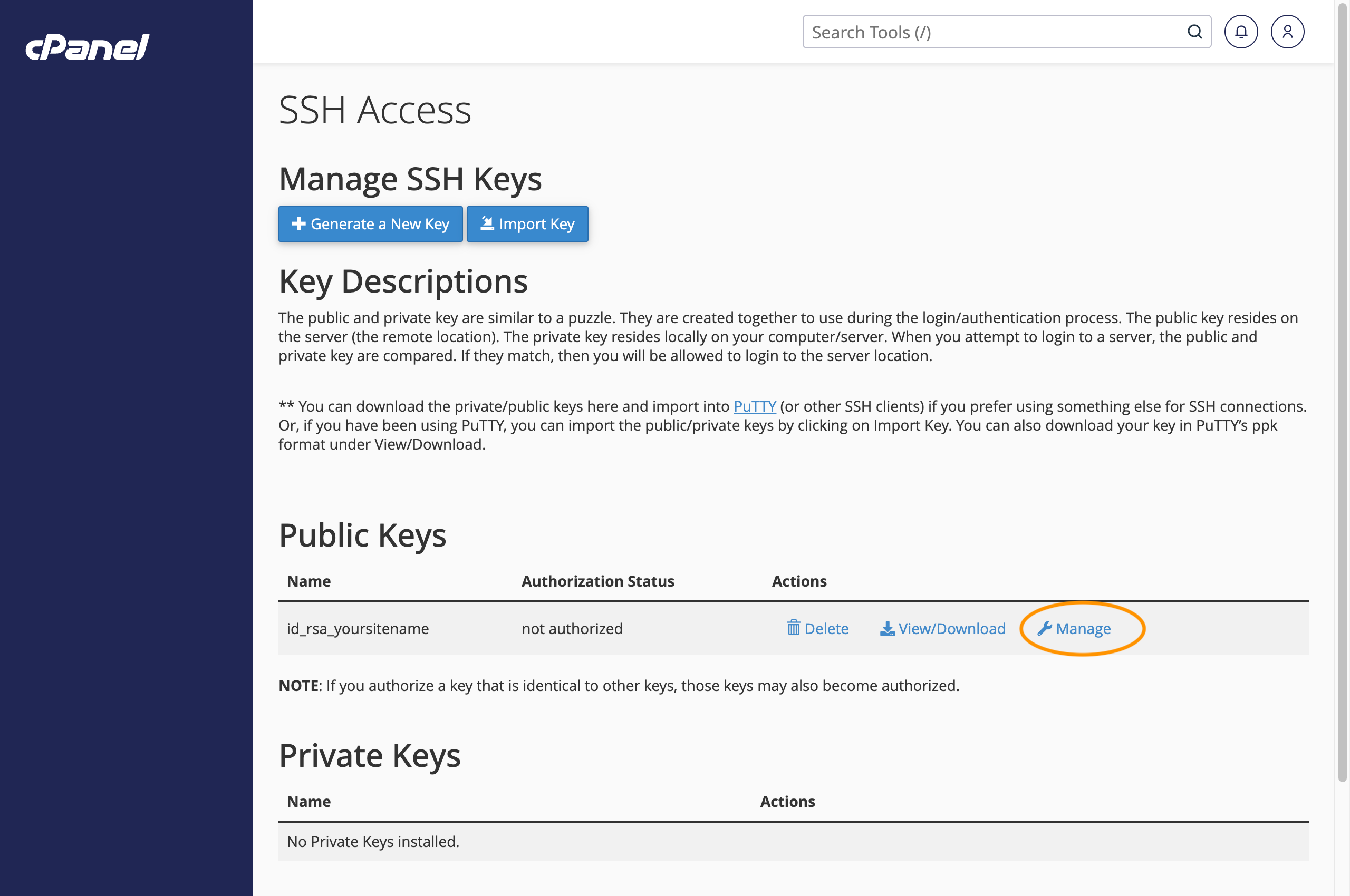
cPanel success message after importing an SSH public key - One last thing, you'll need to back to 'Manage SSH keys' and authorise the key for use. Click 'Manage' to do this
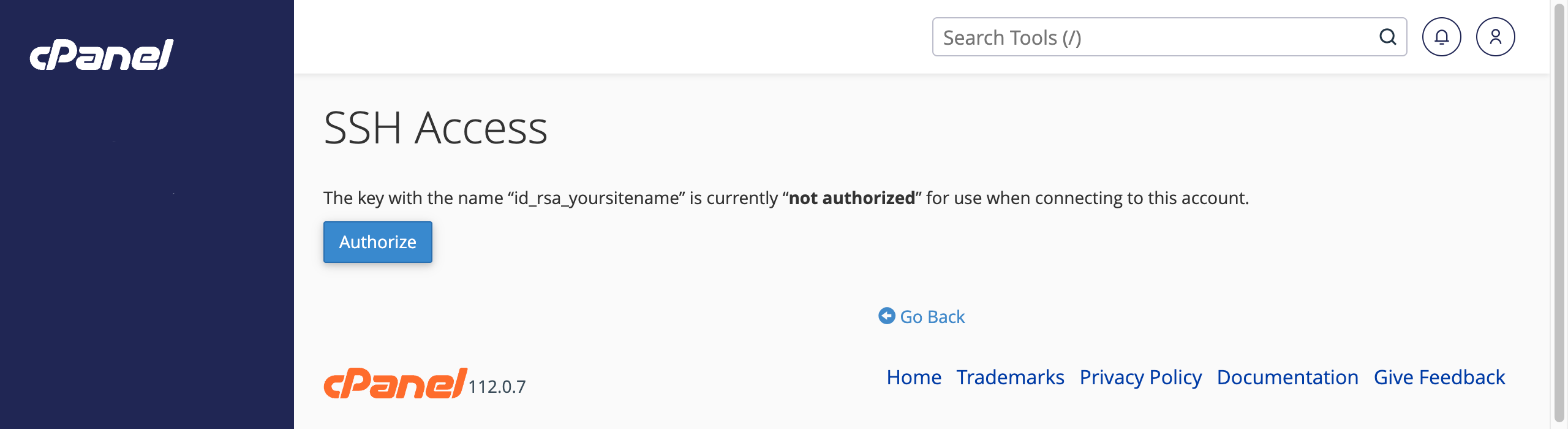
Using cPanel to authorise your newly added SSH key - And then finally click 'Authorise and you are finished!
Finalising authorisation using cPanel - You should get a success message like this
Success, your SSH key is authorised for this site
Testing that it works by using the Joomla Command Line Interface (CLI) to get stuff done
- Use the ssh command with -i to tell it your identity (key file) and then the hostname. If you got it all right you should just be connected to the host! If not then you should check for typos, before delving deeper into other SSH related issues.
% ssh -i ~/.ssh/id_rsa_yoursitename yoursite [username@host ~]$ - Now you can go ahead and play with the Joomla command line interface (CLI).
[username@host ~]$ cd www/cli [username@host ~]$ php joomla.php core:check-updates Joomla! Updates =============== [OK] You already have the latest Joomla version 4.3.3 [username@host ~]$
How cool is that!
Recap of the benefits of key based SSH authentication
- Pause and have a think about the benefits of using SSH keys to enhance Joomla CMS security.
- There are technical advantages in that you are in a secure connection and can't be watched, and there are practical benefits too, in that you no longer need to manage a password.
- Passwordless security is not vulnerable to dictionary attacks or other forms of brute forcing.
Questions to ask yourself
- How does the Secure Shell protocol contribute to your Joomla CMS security?
- What challenges might individuals face when trying to comprehend SSH's complexity and public key encryption?
- How does passwordless secure connectivity enhance the security of trusted computer accounts within a Joomla CMS?

